API authentication is all about verifying who—or what—is trying to access your API. Think of it as a digital bouncer at the door of your club. Its only job is to check IDs and make sure everyone who gets in is actually on the list. This check prevents unauthorized users or systems from accessing your data and services.
Why API Authentication Is Your First Line of Defense
Let's stick with that analogy. If your API is an exclusive, members-only club holding sensitive data or critical business functions, then authentication is your entire security detail. It’s the bouncer, the keycard scanner, and the secret handshake all rolled into one. It's the crucial step of confirming that a client is exactly who they claim to be before they're allowed inside.
Without a solid authentication process, your API endpoints are essentially unguarded doors, leaving your most valuable assets exposed. This isn't just a hypothetical problem. API attacks are exploding, with one report showing a staggering 348% increase in the first half of 2021 alone. That statistic really drives home how critical this protective layer has become.
At its core, authentication is about establishing trust. It lays the foundation for every interaction that follows, including authorization (which is what that trusted user is allowed to do).
When you get authentication right, you ensure that:
- Data stays intact: Only verified users can add, change, or remove data.
- Privacy is upheld: Sensitive user information is kept under lock and key, away from prying eyes.
- Your services are protected: It stops bad actors from overwhelming your API with junk requests or misusing it for malicious purposes.
The chart below shows which authentication methods developers are actually using. As you can see, the industry has a clear favorite.
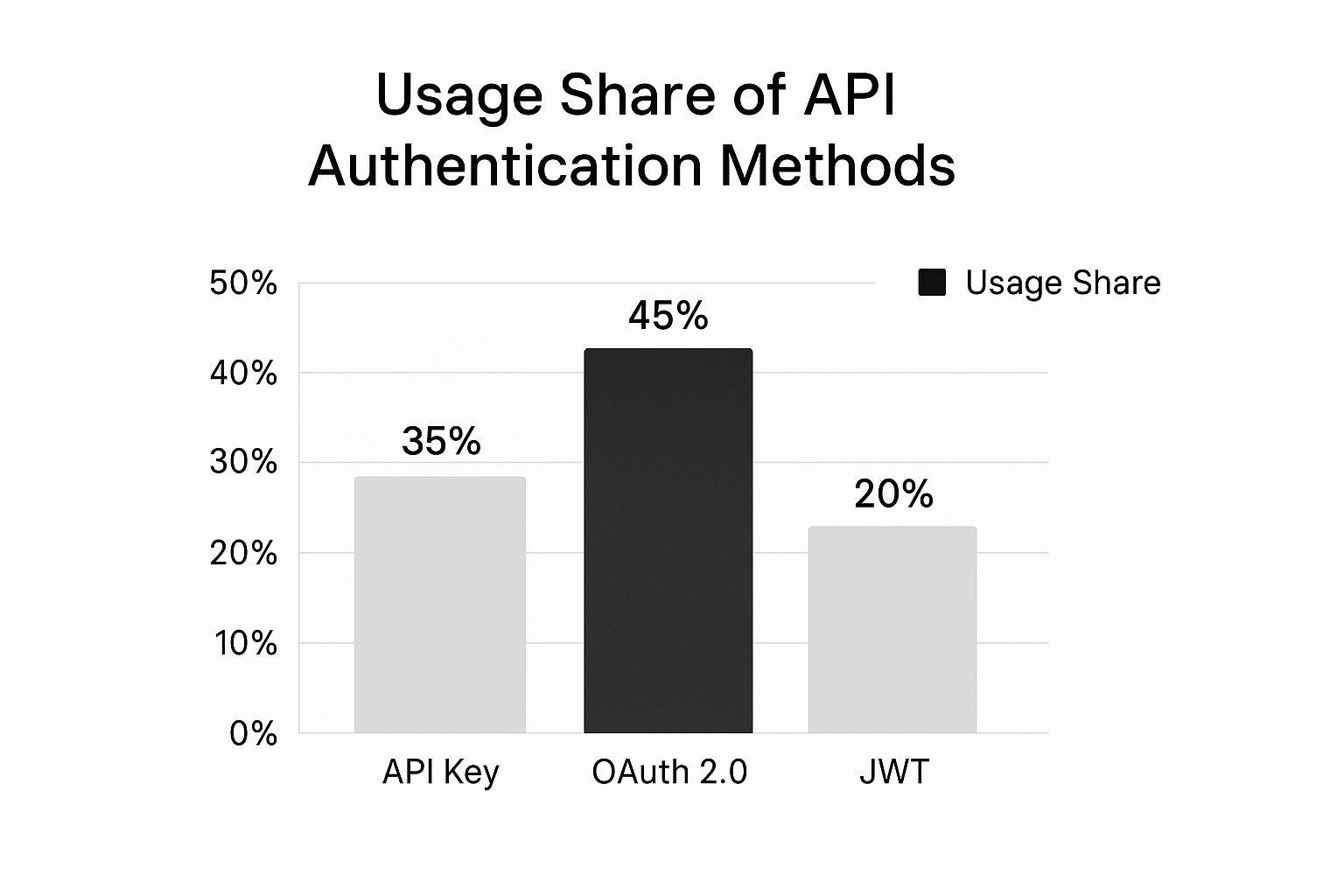
While simple methods like API Keys are still in the mix, it's obvious that the more robust, token-based security of OAuth 2.0 is the dominant choice for modern applications. For a deeper dive into securing user data, especially on mobile, it's worth reviewing these essential mobile authentication best practices.
Choosing the Right Level of Security
No two authentication methods are created equal. Picking the right one always involves a balancing act between security, implementation complexity, and the user's experience. A basic API key might be perfectly fine for a public API that just serves up weather data, but it would be a catastrophic choice for a financial or healthcare app.
Authentication isn’t a one-size-fits-all solution. The right method depends entirely on the context: the sensitivity of the data, the type of client accessing the API, and the potential impact of a security breach.
Getting familiar with the different API authentication methods is your first step toward building applications that are not just functional, but also secure and trustworthy. As we break down each method in this guide, you’ll learn how to pick the perfect "bouncer" for your specific digital club.
To help you get a quick sense of the landscape, here's a high-level comparison of the most common approaches.
Quick Comparison of Common API Authentication Methods
This table gives you a bird's-eye view of the primary authentication methods, comparing what they're used for, how secure they are, and how tricky they can be to set up.
| Method | Best For | Security Level | Complexity |
|---|---|---|---|
| API Key | Simple, public data APIs; internal services | Low | Low |
| Basic Auth | Internal or non-critical applications | Low | Very Low |
| Bearer Token | Mobile and web apps; third-party integrations | Medium-High | Medium |
| OAuth 2.0 | Delegated access; third-party apps accessing user data | High | High |
| OpenID Connect | User authentication on top of OAuth 2.0 | Very High | High |
| Mutual TLS | Business-to-business (B2B) APIs; high-security needs | Very High | Very High |
Think of this table as a starting point. As you'll see in the coming sections, the devil is in the details, and the "best" method truly depends on what you're trying to protect.
Starting with Basic Auth and API Keys
When you first dip your toes into API security, you'll almost certainly run into Basic Authentication and API Keys. These are the most direct, foundational methods for controlling access. Think of them as the front door lock on a house. It's a simple, necessary first line of defense, but you wouldn't rely on just that to protect your most valuable assets.
Basic Auth is exactly as straightforward as its name suggests. It works by bundling a username and password with every single API call. These two pieces of information are combined, encoded using Base64, and then popped into the request's header. It's incredibly easy to set up, but that simplicity comes at a cost. Security is minimal.
Sending credentials with every request is like taping your house key to every letter you mail. If anyone along the delivery route gets a look, they have everything they need to get in. Because of this, Basic Auth is rarely the right call for any public-facing API or service handling sensitive data. It’s best suited for tightly controlled situations, like internal tools or older systems where overhauling security just isn't practical.

Introducing API Keys for More Control
Taking a small but significant step up from Basic Auth, we have the API Key. An API Key is a unique, randomly generated string of characters. It acts like a secret password that identifies a specific application or user trying to access the API. Instead of sending a username and password, the client simply includes this key in the request, usually in the headers or as a query parameter.
This approach is wildly popular, and for good reason:
- It's Simple: Developers can generate a key and get started in minutes. The onboarding process is practically frictionless.
- It's Great for Tracking: Since each key is tied to a specific user or project, it’s an effective way to see who is using your API and how much.
- It Offers Easy Access Control: If a key is ever compromised or no longer needed, you can revoke it instantly without disrupting any other users.
But API Keys aren't a silver bullet. They share a critical vulnerability with Basic Auth: if the key is exposed, it grants immediate access. That's why you must always transmit them over a secure (HTTPS) connection and never, ever embed them directly in client-side code, like the JavaScript on a public website. For a deeper dive into implementation, the Refgrow authentication documentation offers some solid best practices.
When to Use These Simple Methods
So, where do these simpler methods fit into a modern developer's toolkit? Their real value shines in situations where simplicity trumps the need for ironclad security.
Key Takeaway: With Basic Auth and API Keys, you're always making a trade-off: simplicity for security. They're perfect for low-risk environments but fall short when it comes to protecting sensitive data or mission-critical functions.
They're a great fit for use cases like:
- Internal Services: Perfect for when two services you own need to talk to each other inside your own secure network.
- Public Data APIs: Ideal for providing non-sensitive info, like weather forecasts or city bus schedules, where your main goal is tracking usage, not locking down data.
- Developer Sandboxes: A quick and easy way to let developers start experimenting with your API in a safe, controlled test environment.
Ultimately, while Basic Auth and API Keys are essential to know, they’re just the first rung on the API security ladder. They solve the basic problem of "who are you?" but lack the nuance and strength required for most of today's applications.
Mastering Tokens with OAuth 2.0
If an API Key is the simple lock on your front door, then OAuth 2.0 is the high-tech key card system at a modern hotel. It’s a huge leap forward in how we manage access to sensitive data and is rightly seen as the gold standard for many of today's APIs.
So, what problem does it solve? It answers a critical question: how can you let a third-party application use your data without handing over your password?
Think about it. You’ve just discovered a cool new photo editing app that can pull images directly from your Google Photos. You definitely don't want to give that app your Google username and password. That would be like giving the hotel concierge a master key to every single room—a massive security nightmare waiting to happen.
This is where OAuth 2.0 steps in, acting like a secure valet. You (the user) tell the hotel front desk (in this case, an authorization server like Google) that you’re giving the valet (the photo app) temporary access to a specific room (your photos).
The front desk then issues a special, temporary key card—an access token—to the valet. This key card only opens that one room, and it expires after a short time. The valet never learns your master password and can only do what you’ve explicitly permitted. This whole process is called delegated authorization, and it's the brilliant idea at the heart of OAuth 2.0.
The Key Players in the OAuth Flow
To really get a handle on OAuth 2.0, you need to know the cast of characters involved in this security dance. While the technical nitty-gritty can be deep, the roles themselves are pretty easy to grasp.
- Resource Owner: That’s you! You own the data (your photos, contacts, files) and you're the only one with the authority to grant access to it.
- Client Application: This is the third-party app that wants to use your data, like the photo editing app from our example.
- Authorization Server: Think of this as the central authority. It’s the service that manages your account, like Google, Facebook, or GitHub. Its job is to authenticate you and, with your permission, issue the access tokens.
- Resource Server: This is the API where your data actually lives. It's the server the client application ultimately wants to talk to and will only unlock the data if it receives a valid access token.
The entire flow is a carefully choreographed interaction between these four parties, making sure that access is granted securely and only with your explicit consent.
The real power of OAuth 2.0 is that it separates the user's credentials from the application's access. The app gets a temporary token, not your password, which drastically reduces the risk if that application is ever compromised.
Scopes and Consent: Putting You in Control
One of the most powerful features of OAuth 2.0 is the concept of scopes. When our photo app asks for permission, it doesn't just ask for generic access. It has to specify exactly what it wants to do.
For example, it might request the photos.read scope (to view your photos) but not the photos.delete scope.
This gives you, the resource owner, incredibly fine-grained control. That consent screen you see whenever you "Log in with Google" is actually listing these requested scopes and asking for your direct approval. You can review the request and decide whether to approve or deny it, putting you firmly in the driver's seat. It's a massive improvement over older methods that often demanded an all-or-nothing approach to your data.
From Authorization to Authentication with OIDC
OAuth 2.0 is brilliant for authorization (what an app is allowed to do), but it wasn't originally built for authentication (verifying who a user is). This important distinction led to the creation of OpenID Connect (OIDC), which is an identity layer built right on top of OAuth 2.0.
By 2025, OpenID Connect has solidified its place as a leading protocol for managing user identities in both web and mobile apps. OIDC extends the OAuth flow to give applications a standardized way to confirm your identity, enabling features like Single Sign-On (SSO) and a more connected identity ecosystem. You can dive deeper into how OIDC is central to modern security in this detailed overview of top authentication methods on LoginRadius.com.
In short: if OAuth 2.0 gives an app a key to your hotel room, OIDC provides a verified ID card that proves who is holding that key. Together, they form the secure foundation for much of the modern internet.
Decoding JWT and OpenID Connect
Now that we've covered the basics of the OAuth 2.0 authorization framework, let's dive into two closely related technologies that are absolutely essential for modern API security: JSON Web Tokens (JWT) and OpenID Connect (OIDC). Think of it this way: if OAuth gives you a temporary key card to access a building, JWT and OIDC are what verify your identity and the credentials on that card.
I like to explain JWTs (pronounced "jots") as a kind of self-contained digital passport. A normal passport has to be checked against a central database every time you use it, but a JWT carries all the necessary verification information right inside itself. It’s essentially a compact, URL-friendly string that securely passes verified information between two parties.
The Anatomy of a Digital Passport
A JWT isn’t just a random jumble of characters. It's carefully built with three distinct parts, each separated by a period.
- Header: The first part usually specifies the algorithm used to sign the token, like HMAC SHA256 or RSA. This is like the cover of the passport, telling you what kind of passport it is and what security features it has.
- Payload: This is the heart of the token, where the verified information, or claims, are stored. This data can include the user's ID, their role (like "admin"), and when the token expires. It’s the main content of the passport, holding all the bearer's verified details.
- Signature: To make sure the passport hasn't been tampered with, this final part is a digital signature. It's created by combining the encoded header, the encoded payload, and a secret key, then running it through the algorithm from the header. This signature guarantees the token's integrity.
This self-contained structure is the secret sauce behind stateless authentication. Because the token itself holds all the necessary data, the server doesn't have to constantly check a database to validate the user's session with every single request. This is a huge win for performance, dramatically cutting down on server load and making JWTs perfect for distributed systems and microservices where scalability is key.
The JWT.io debugger has a fantastic tool that shows this structure perfectly.

On the left, you can see the long, encoded token string. The right side shows it decoded, breaking it down into the header, payload, and signature so you can see exactly what's inside.
From Authorization to Authentication with OIDC
While JWTs are a fantastic, secure format for tokens, they don't actually define a complete authentication process on their own. This is where OpenID Connect (OIDC) steps in. It was specifically designed to fill a crucial gap left by OAuth 2.0.
Key Distinction: OAuth 2.0 is for authorization (what you're allowed to do). OpenID Connect is for authentication (proving who you are).
OIDC is a simple identity layer built right on top of the OAuth 2.0 protocol you already know. It adds a standardized authentication flow, letting applications verify a user's identity based on the authentication done by an Authorization Server. To do this, it cleverly extends the OAuth 2.0 flow by introducing a new kind of token: the ID Token.
This ID Token is simply a JWT that contains verified claims about the user—things like their name, email, and a unique ID. When a client application requests the openid scope during the OAuth flow, it's telling the server, "Hey, I need to authenticate this user, not just get access to something." In return, the server sends back both an access token (for authorization) and an ID token (for authentication).
This elegant combination gives us some powerful advantages:
- Simplified User Authentication: It creates a standard, interoperable method for handling user logins across countless different platforms.
- Enhanced Security: It builds on the battle-tested security of OAuth 2.0 while adding a dedicated layer for identity verification.
- Single Sign-On (SSO): OIDC is the engine that powers most of the SSO experiences you use every day. Once you log in with a provider like Google or Microsoft, you can access tons of other apps without having to type your password again.
Ultimately, JWT and OIDC aren't competing api authentication methods; they're partners that work together. JWT is the format—the passport itself. OIDC is the process—the standardized system for issuing and validating that passport to confirm your identity. Together, they form a rock-solid foundation for building secure, user-friendly applications.
5. Securing High-Stakes and Enterprise Systems

When the stakes are incredibly high, standard security just won't cut it. For industries like banking, healthcare, or critical B2B services, you need authentication methods built for maximum trust. We're talking about scenarios where a security breach isn't just an inconvenience—it's a catastrophe.
These advanced methods go beyond simply checking if a user or app has the right password. Their entire purpose is to establish undeniable, ironclad trust between systems. This is where specialized tools like Mutual TLS (mTLS) and Security Assertion Markup Language (SAML) step in, providing the heavy-duty controls needed for true enterprise-grade security.
Mutual TLS: The Two-Way Digital Handshake
Imagine a top-secret meeting where both spies must present a unique, coded medallion to prove their identity before a single word is spoken. That’s the core concept behind Mutual Transport Layer Security (mTLS).
With standard TLS (the "S" in HTTPS), your browser verifies the website's identity to make sure it's legitimate. mTLS takes this a massive step further. In an mTLS handshake, both the client and the server present digital certificates to each other, and a trusted authority validates both. This two-way verification creates an exclusive, ultra-secure channel, ensuring both parties are exactly who they claim to be.
With mTLS, trust is never assumed; it is mutually proven. This all but eliminates the risk of man-in-the-middle attacks and guarantees that only pre-approved, certified systems can even talk to your API.
This approach is non-negotiable for:
- Financial Transactions: Locking down communication between banks and payment gateways.
- IoT Devices: Ensuring that only authorized smart devices can connect to a central hub.
- Internal Microservices: Guaranteeing that services within your own network are communicating securely.
While managing the certificates can be complex, the unmatched security of mTLS makes it the gold standard for protecting the most sensitive data exchanges. To build a truly robust defense, it's also crucial to follow essential app security standards.
SAML: The Standard for Enterprise Federated Identity
If mTLS is the bodyguard for system-to-system communication, then Security Assertion Markup Language (SAML) is the seasoned veteran of enterprise user access. It’s an open standard that lets a trusted Identity Provider (like a company's internal user directory) vouch for a user and grant them access to a separate Service Provider (like a third-party cloud app).
Think of it like using your corporate ID badge to get into a partner company's building. Your company (the Identity Provider) tells the building's security (the Service Provider) that you're a verified employee who is cleared for entry. This process, known as federated identity, is the engine behind most corporate Single Sign-On (SSO) systems.
It's a mature, XML-based solution that large organizations rely on to manage user access across dozens of internal and external applications from one central place. This simplifies life for users and gives IT powerful security oversight.
The Push for Stronger, Simpler Authentication
The demand for more robust authentication is exploding. A key component of any advanced security strategy is often multi-factor authentication (MFA). In fact, the global MFA market, valued at $10.3 billion in 2020, is projected to soar to $40 billion by 2030.
This growth is also fueling the move toward passwordless methods like WebAuthn, which uses biometrics (your fingerprint or face) or physical hardware keys (like a YubiKey). WebAuthn offers a far more secure and user-friendly experience than typing passwords, making it a fantastic choice for modern apps that refuse to compromise on either security or usability.
For a complete look at all our security features and best practices, dive into our comprehensive security documentation.
So, you’ve got a handle on the different API authentication methods. That’s the easy part. The real challenge—where the rubber meets the road—is picking the right one for your specific project.
Get it wrong, and you could be looking at a serious security hole or a clunky, frustrating experience for your users. The trick is to stop thinking about it as a menu of options and start thinking with a practical, decision-driven mindset. This all starts by asking the right questions about what you’re actually trying to build.
Key Questions to Guide Your Decision
Before you write a single line of code, get your team together and hash out the answers to these questions. There are no perfect answers here, just a series of trade-offs.
- How sensitive is the data? Are we talking about public, low-stakes information like weather reports? Or are we protecting highly sensitive financial records or personal health information? The more valuable the data, the beefier your authentication needs to be.
- Who is the "user"? Is it an internal microservice talking to another? A person logging into your app? Or a third-party developer building on top of your platform? Each one of these has a completely different risk profile and set of expectations.
- What kind of user experience are you aiming for? Do your enterprise customers need a seamless Single Sign-On (SSO) experience? Or is your main goal to give developers a quick and painless way to generate an API key and get started?
- What's your team's bandwidth? Let's be honest about this one. Do you have the in-house expertise to correctly implement a complex protocol like OAuth 2.0, or would managing a certificate-based system like mTLS stretch your resources too thin?
Answering these questions honestly keeps you from over-engineering a solution for a simple, low-risk API. More importantly, it prevents you from under-securing a high-stakes one. If you need a refresher on how all these pieces fit together, our API overview documentation provides some excellent high-level context.
The goal isn’t to pick the "most secure" method in a vacuum. It's to choose the most appropriate one for your reality. The right choice is a perfect blend of data sensitivity, user needs, and your team's capabilities, creating a security posture that actually works in the real world.
To make this even more concrete, let's look at how specific, everyday scenarios map to different authentication methods. Think of the table below as a quick cheat sheet for making a confident decision.
Decision Framework for API Authentication
This framework will help you select the best authentication method by matching it to common application requirements and constraints you're likely to face.
| Scenario | Recommended Method(s) | Key Considerations |
|---|---|---|
| Public Data API | API Keys | The name of the game is simplicity. You want to prioritize a great developer experience and easy usage tracking. Security is less of a concern than accessibility. |
| Mobile Banking App | OAuth 2.0 with OIDC | Here, security is everything. You need to know who the user is (authentication) and control exactly what they can do (authorization). |
| Internal Microservices | JWT or mTLS | It’s all about speed and trust. JWTs are fantastic for stateless, efficient communication, while mTLS offers an ironclad, mutually verified connection between services. |
| Third-Party App Store | OAuth 2.0 | You need a way to let external applications access user data on their behalf—securely, and without ever sharing the user's actual password. |
By walking through the key questions and using this framework as a guide, you're not just guessing. You're making an informed, strategic decision that sets your project up for success from the start.
Common Questions About API Authentication
As you get your hands dirty with APIs, a few questions always seem to pop up. Let's tackle some of the most common points of confusion to make sure you're on solid ground.
What's the Real Difference Between Authentication and Authorization?
It’s incredibly common to see these two terms used interchangeably, but they are fundamentally different concepts. Getting this right is key.
Authentication is all about identity. It’s the process of proving you are who you claim to be. Think of it like showing your driver's license at a bank to prove your identity before you can access your account.
Authorization, on the other hand, comes next. It's about permissions. Once the bank knows who you are (authentication), authorization determines what you're allowed to do—can you withdraw cash, check your balance, or apply for a loan?
In short: Authentication asks, "Who are you?" Authorization asks, "What are you allowed to do?"
Can I Use More Than One Authentication Method at a Time?
Absolutely, and in many cases, you should. Combining methods is a powerful security practice often called layered authentication. This approach creates multiple security checkpoints, making it much harder for an attacker to succeed.
For instance, an application could require a static API Key to identify itself, but also an OAuth 2.0 token to confirm the specific user has granted permission. This creates a defense-in-depth security model. If one layer fails—like a leaked API key—the other layer is still there to protect the system.
How Does Rate Limiting Fit into All This?
Rate limiting isn't strictly an authentication method, but it's an essential sidekick. It’s all about controlling how often a user or client can hit your API within a certain window of time. Think of it as a bouncer at a popular club who only lets a certain number of people in every minute to prevent overcrowding.
This is critical for a few reasons:
- Stops Abuse: It prevents a single bad actor from flooding your server with requests, which could knock it offline in a denial-of-service (DoS) attack.
- Ensures Fair Use: It makes sure that one power user doesn’t hog all the server resources, ensuring a smooth experience for everyone else.
- Adds Security: It’s a great way to shut down brute-force attacks where someone tries to guess a password by making thousands of login attempts in a short time.
When you use rate limiting alongside your chosen api authentication methods, you create a much tougher, more reliable system.
Ready to build and scale your own referral program without the technical overhead? With Refgrow, you can embed a fully native affiliate dashboard into your SaaS in minutes. Launch your affiliate program today.
